-
PRODUCT FEATURES
-
WEB-BASED
- Why SMEs Should Use an ERP?
- All features
- Affordable ERP
- Web-based ERP
- Task Automization
- Unlimited Users
- Free System Upgrades
- Customizable Reports
- Menu Optimization
- Flexibly Configurable Board
- Mobile App
- Corporate Messenger
- e-Contract
- Excel Bulk Upload
- ECOUNT Open API
- Server Security
- Data Tracking
- Multilingual Support
- Business Management
- INVENTORY
- PRODUCTION
- SALES
- PURCHASING
- ACCOUNTING
- PAYROLL
- COLLABORATE
-
WEB-BASED
- EXPLORE
- PRICING
- SERVICES
- ABOUT US
- ETC
Use easily, and check everything immediately!
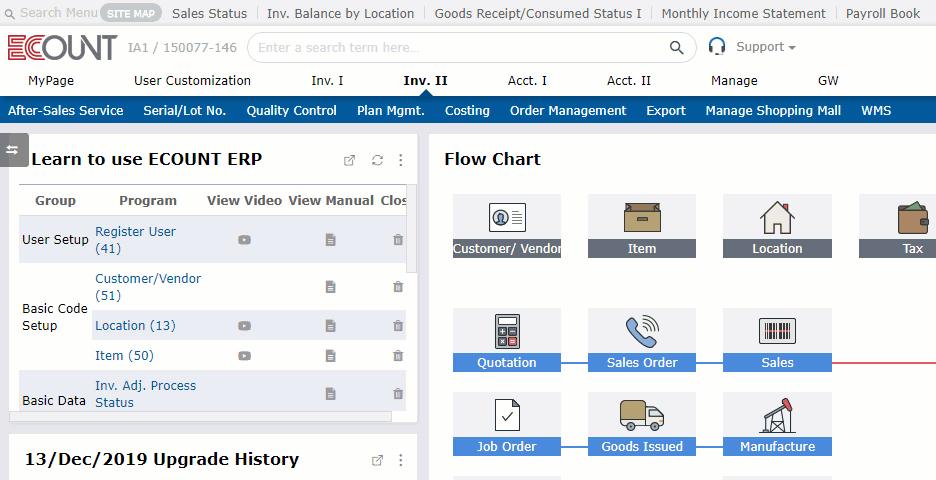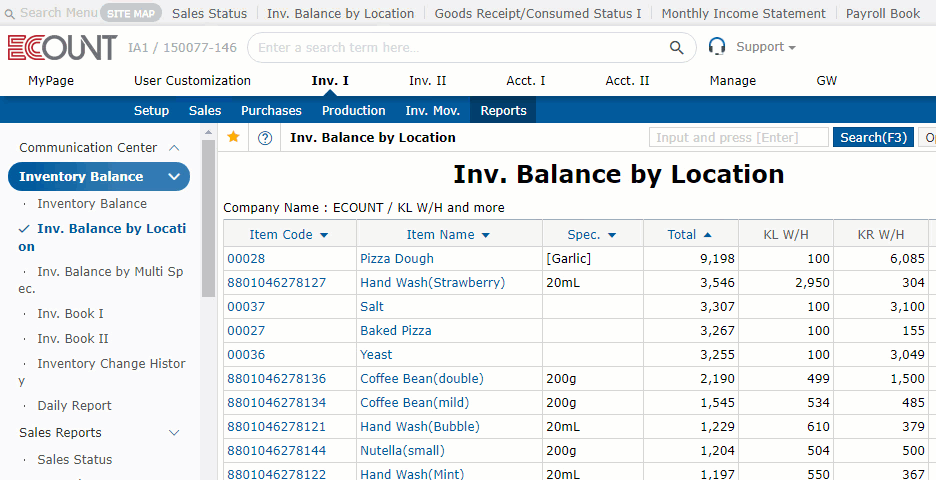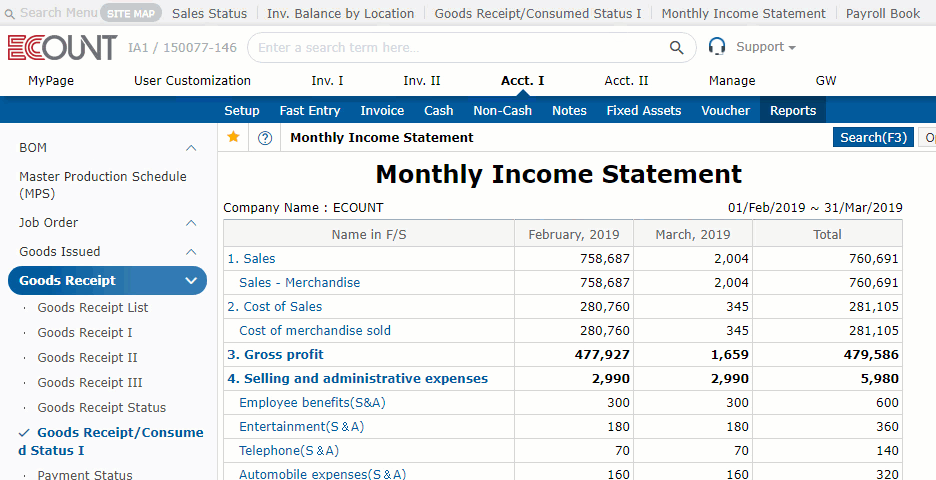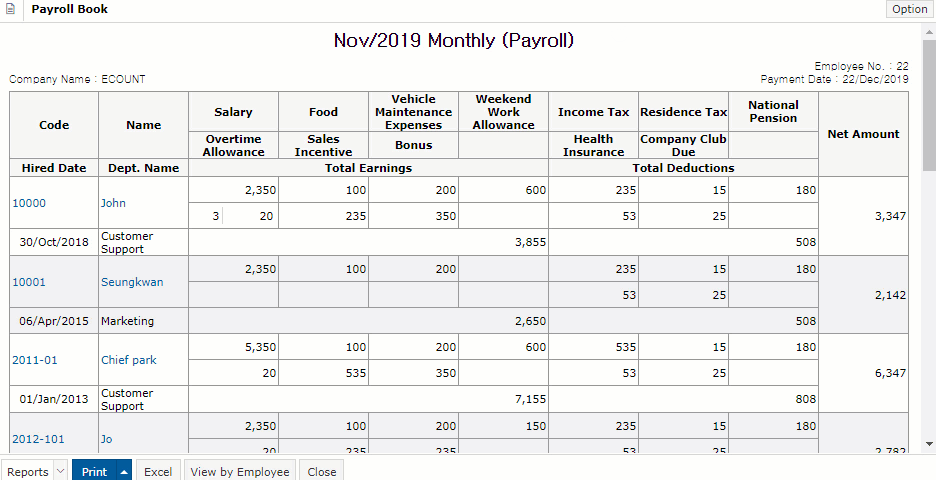
Real-time reporting
Any entered data are immediately
reflected on reports in real-time.
View the latest report right away.
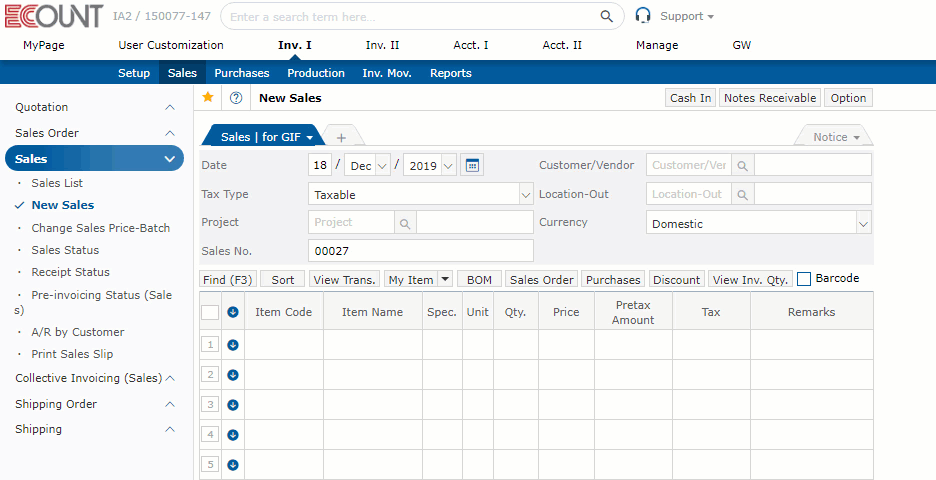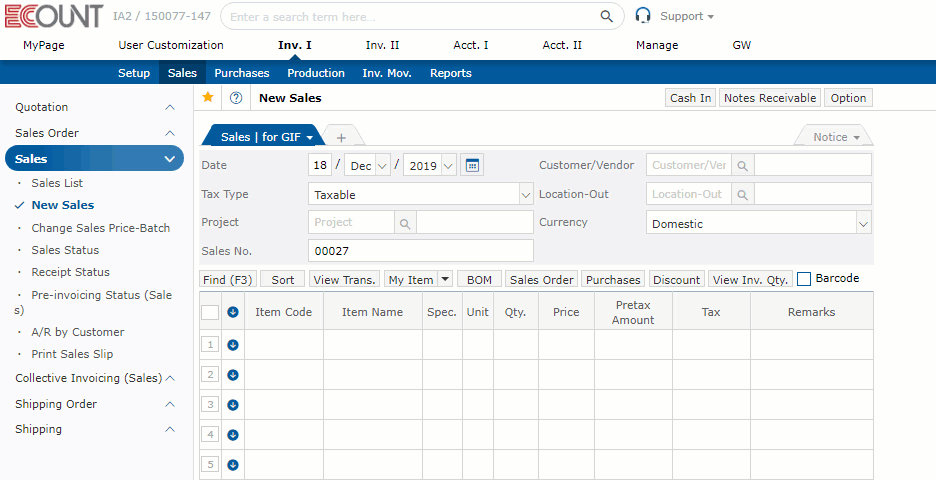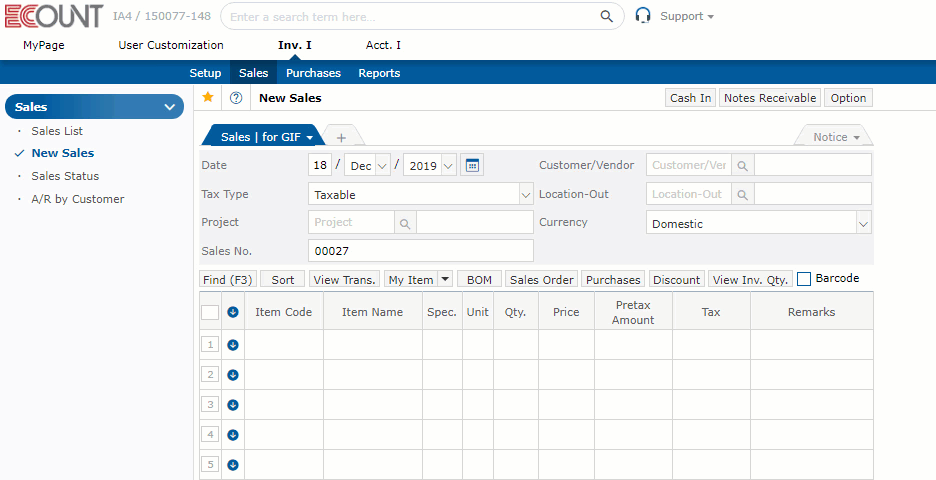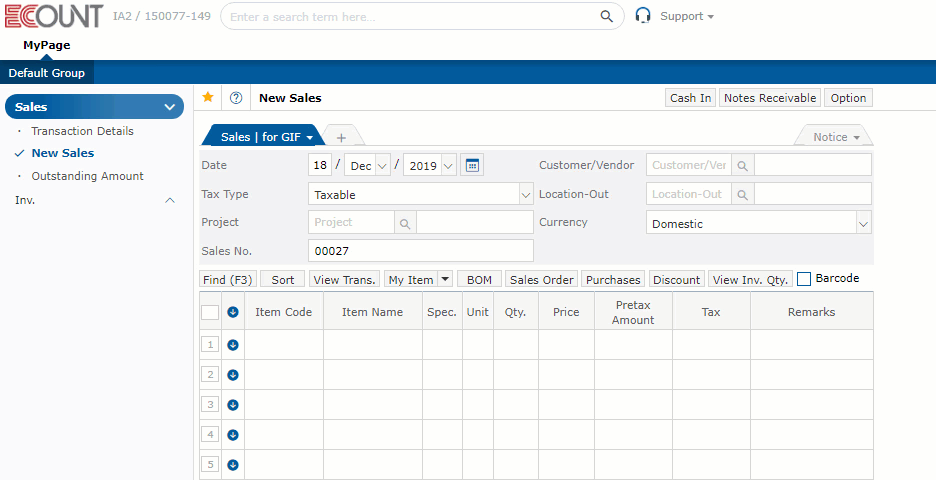
Simply use only the menus you need!
Menus can be easily re-configured
for your use.
Select and use only the menus you need.
Already, 80,000 companies from all industries
are using ECOUNT.
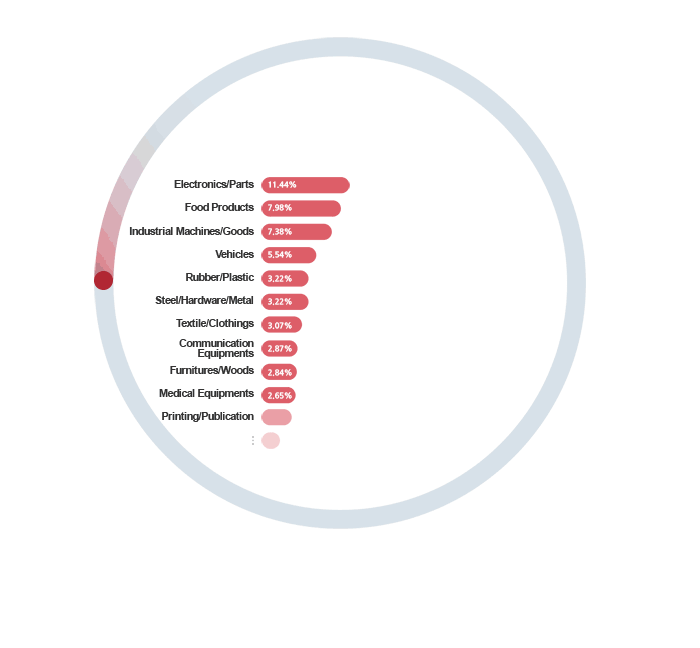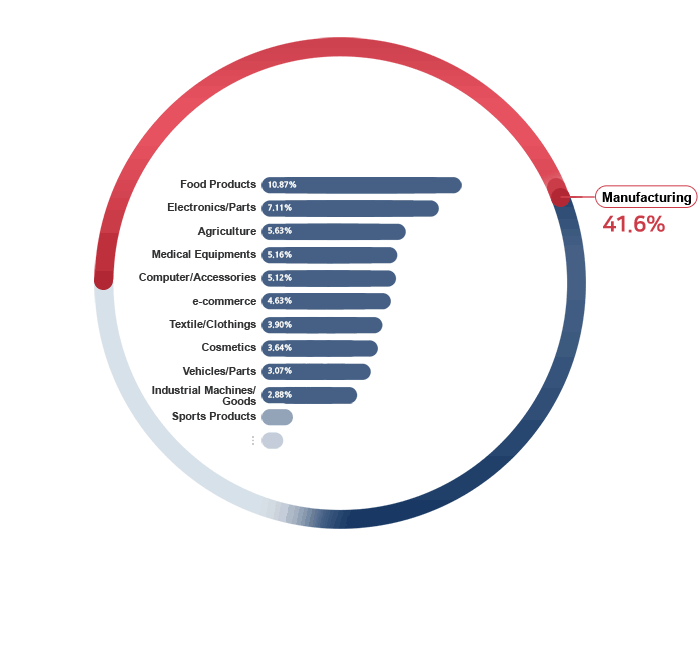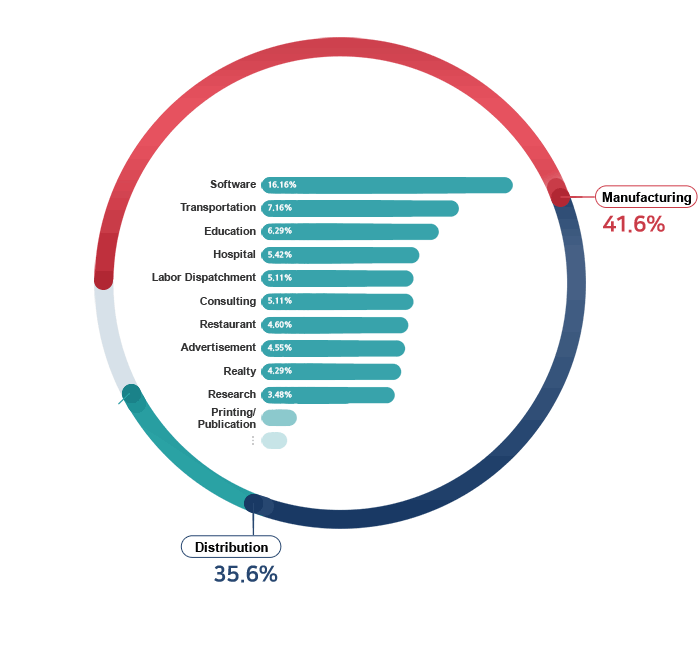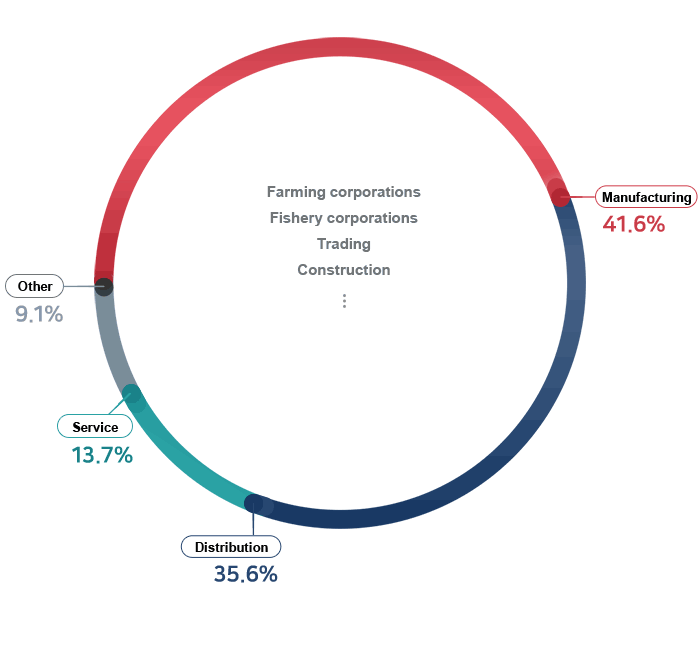
Why do so many companies choose ECOUNT?
-
100% Web-based
Use freely on any device,
anytime, anywhere with internet access -
Unlimited users
No additional cost
for the number of ERP users -
Free additional services
Various free additional services
such as mobile app,
and corporate messenger -
Feature upgrades
Continuous free feature upgrades,
new features updated reflecting
revised tax laws and customer suggestions -
Full utilization of required features
2 free on-site training sessions
Real-time customer support
Video lectures, group training
All ECOUNT ERP Features